Risk management framework
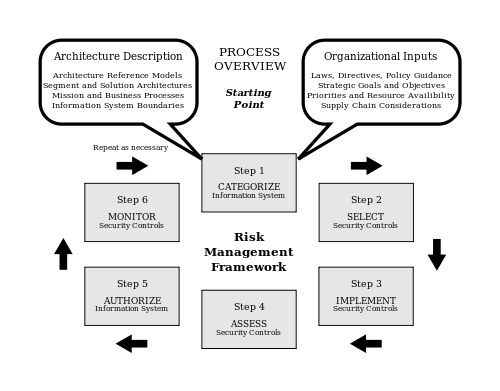
The Risk Management Framework (NIST Special Publication 800-37).
NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems", developed by the Joint Task Force Transformation Initiative Working Group, transforms the traditional Certification and Accreditation (C&A) process into the six-step Risk Management Framework (RMF).
The Risk Management Framework (RMF), illustrated at right, provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle.[1]
The RMF steps include:
- Categorize the information system and the information processed, stored, and transmitted by that system based on an impact analysis.
- Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on an organizational assessment of risk and local conditions.
- Implement the security controls and describe how the controls are employed within the information system and its environment of operation.
- Assess the security controls using appropriate assessment procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
- Authorize information system operation based on a determination of the risk to organizational operations and assets, individuals, other organizations, and the Nation resulting from the operation of the information system and the decision that this risk is acceptable.
- Monitor the security controls in the information system on an ongoing basis including assessing control effectiveness, documenting changes to the system or its environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to designated organizational officials.
See also
- Department of Defense Information Assurance Certification and Accreditation Process, previous program
- NIST Special Publication 800-37, "Guide for Applying the Risk Management Framework to Federal Information Systems"
- NIST Special Publication 800-53, "Security and Privacy Controls for Federal Information Systems and Organizations"
References
- ↑ Guide for Applying the Risk Management Framework to Federal Information Systems
External links
- NIST Special Publication 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems
- Content of the framework proposed in the ISO 31000 Risk Management Standard
- Top 10 Sources of RMF Policy and Guidance
This article is issued from Wikipedia - version of the 8/26/2016. The text is available under the Creative Commons Attribution/Share Alike but additional terms may apply for the media files.